Key Takeaways
- Bluetooth smartwatches use Bluetooth Low Energy (BLE) technology and advertising packets called beacons to connect to smartphones, allowing for convenient access to notifications and other features.
- Smartwatches are vulnerable to various security threats, such as malicious applications that can manipulate data and firmware exploits that can cause damage.
- To protect your smartwatch, conduct thorough research on its security implementations before purchasing, keep firmware updated, avoid installing unknown or unverified apps, and enable pairing by PIN for added security. Bluetooth encryption is crucial for keeping data secure.
Bluetooth smartwatches have become an integral part of many of our daily lives, providing convenient access to notifications, fitness tracking, and even phone calls, all from our wrists. As these wearable devices continue to evolve, it's crucial to address an essential question: Can your Bluetooth smartwatch be hacked?
How Bluetooth Smartwatches Work
Bluetooth smartwatches connect to your smartphone via a technology called Bluetooth Low Energy (BLE) that uses the same band as regular Bluetooth but uses different channels for data transmission. To be specific, it uses 40, 2300 to 2.4835 MHz channels.
The primary difference between regular Bluetooth and BLE is that it consumes much less power than the regular BT protocol as one may figure out from the name itself. BLE devices, in this context, your smartwatch, communicate by transmitting advertising packets called beacons.
These beacons advertise the existence of your smartwatch to in-range devices. A device that is listening for those beacons, which in this case, is your smartphone, responds to an advertising packet with a SCAN request. The smartwatch then responds to the SCAN request with more data.
How the data between your smartwatch and smartphone is structured is defined by the Generic Attribute Profile or, GATT. The GATT has a list of the device’s features, characteristics, and services, which allow for a listening device to establish the advertising device’s functionality and how to trigger different actions. Attackers, if able to intercept the advertising device’s beacons will also be able to inspect and then strategically abuse the information present in GATT.
Common Security Threats and Vulnerabilities
Bluetooth smartwatches are subject to various threats and vulnerabilities. Here are some common attacks:
- Malicious Applications: Smartwatches are extensively app-centric. An application on your smartwatch is responsible for dictating how your smartwatch functions. A master-slave relationship is established between the app and the smartwatch. Your smartwatch trusts and executes all commands sent by the controller app. If an attacker were to hijack the app and inject malicious code into it, they’d potentially be able to manipulate the data and functionality of the smartwatch.
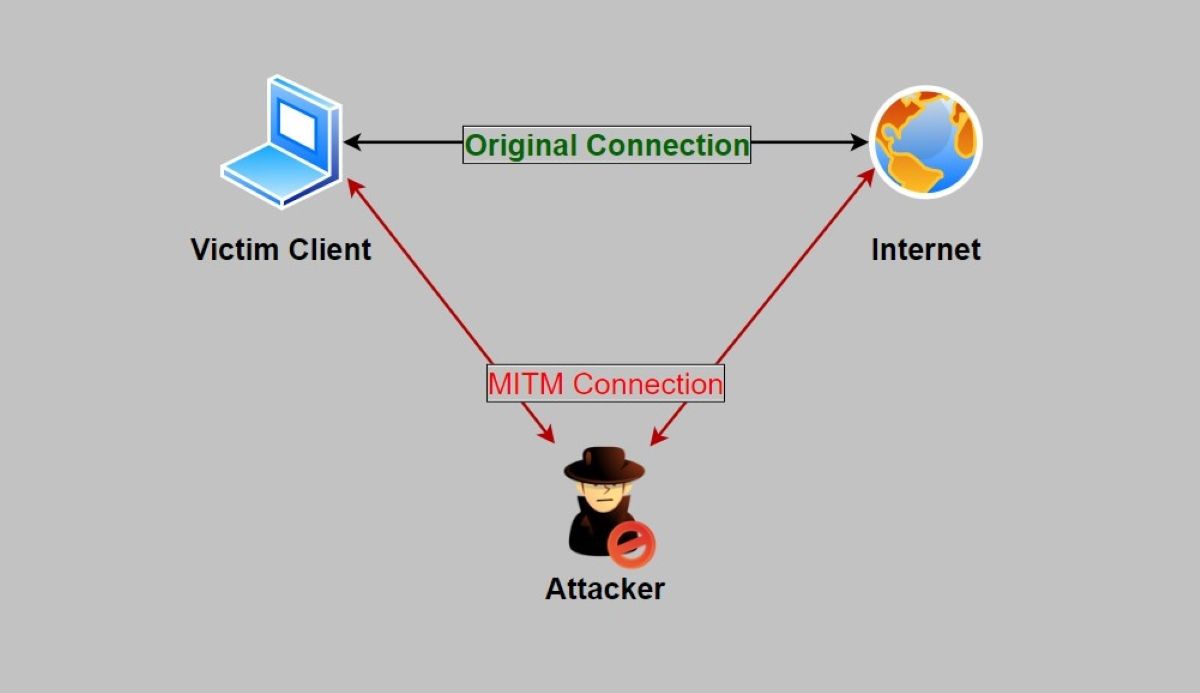
- MITM Attacks: Cheap smartwatches generally don’t implement any form of encryption on the data exchanged between your smartphone and the smartwatch, making it easy for attackers to perform a Man-In-The-Middle (MITM) attack and intercept and inspect the information.
- Moreover, once an attacker can figure out how to trigger certain functionality in your smartwatch, they can then send malicious packets to your smartwatch to manipulate it. For example, an attacker can change the date and time of your smartwatch with ease or, worse, force update the firmware of your smartwatch.
- Firmware Exploits: Firmware is a piece of immutable low-level software that’s responsible for making sure that your smartwatch functions properly. It is in control of everything on your smartwatch. Sometimes, there might be vulnerabilities in the firmware which could be leveraged to cause damage.
How to Protect Yourself
Before you purchase a smartwatch, be sure to conduct thorough research on its history of vulnerabilities and security implementations along with its other features. Avoid purchasing lower-end smartwatches, and if you do, try to keep the smartwatch unpaired if you’re going out of your home. Besides these practices, here are a few crucial steps to follow:
- Keep the firmware of your devices updated. As soon as a new firmware update drops, be sure to install it.
- Make sure that you’re not installing any unknown applications from shady websites or using cracked apps, since unverified apps can compromise your device.
- If possible, enable pairing by PIN so that your smartwatch only pairs with your trusted devices after a security PIN is entered.
Now You Know How to Keep Your Bluetooth Smartwatch Secure
Smartwatches are great gadgets to boost your productivity, track your health, or just carry around as a fashion piece. However, without the proper implementations in place, your smartwatch could fall prey to adversaries. The major issue with most smartwatches is the lack of an encryption layer on the traffic. Bluetooth encryption is crucial to keeping your data secure.